Create a new OAuth2 M2M Impersonation client
Introduction
In this tutorial, you are going to learn how to create a machine-to-machine impersonation OAuth2 client on your Qlik Cloud tenant through the management console user interface.
If you’re not sure which type of OAuth client you need for your application, review the OAuth2 Overview to learn more.
Requirements
- A Qlik Cloud tenant
- Tenant Admin role assigned to the user account creating OAuth2 clients
Create an OAuth2 client application in Qlik Cloud
Access the management console and select OAuth.
Click Create new, then select Web from the Client type dropdown.
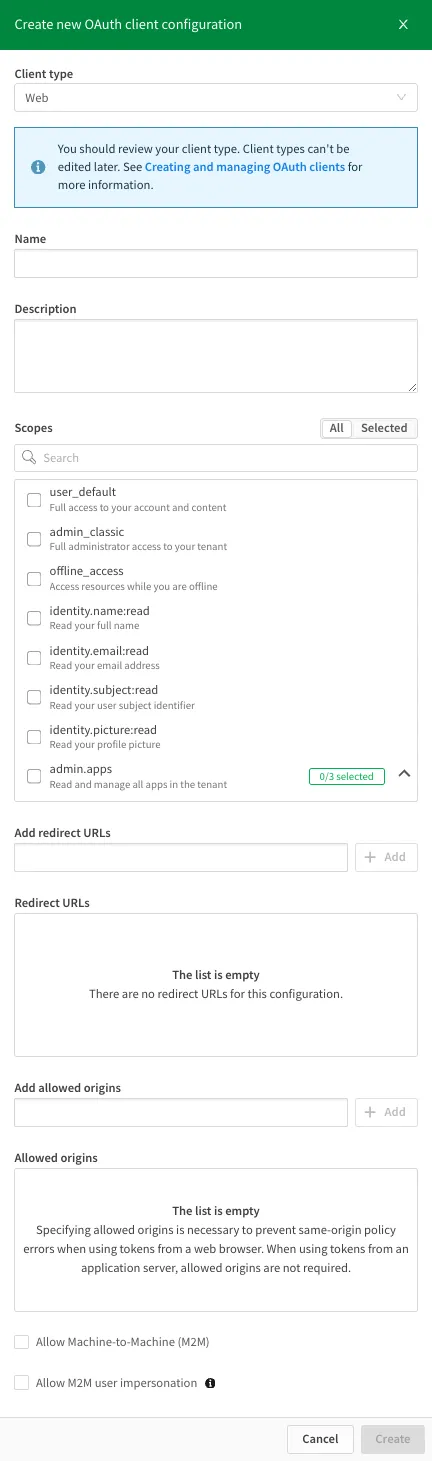
Enter a name for the OAuth2 client.

Select the scopes to grant to the client from the Scopes list.
More information about available scopes can be found at OAuth Scopes.
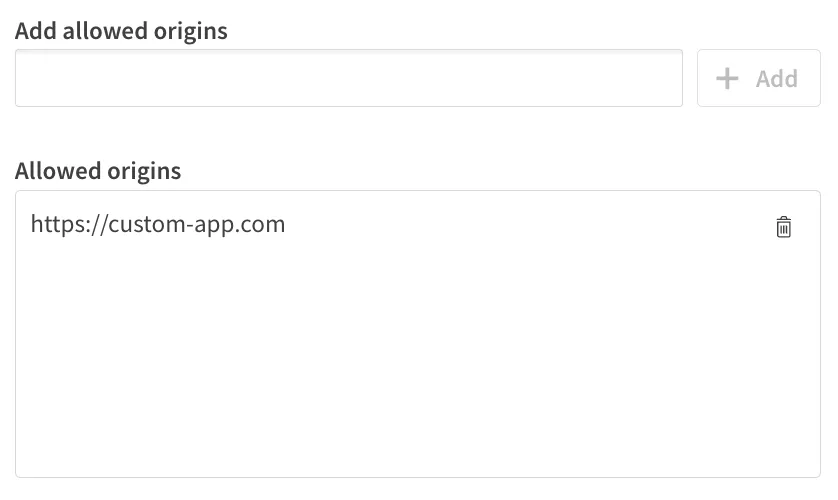
If you plan on using the access token from a browser application, add it to the Allowed Origins list.
In this example, https://custom-app.com will be using impersonation tokens to make requests to a Qlik Cloud tenant.
Select the checkbox to enable the OAuth client to act as a machine-to-machine impersonation application.
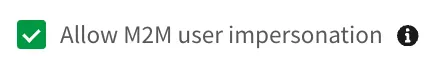
Click Create. A window appears containing the Client ID and Client secret values for the OAuth2 client application to use. Copy and paste them to a secure location for later use.
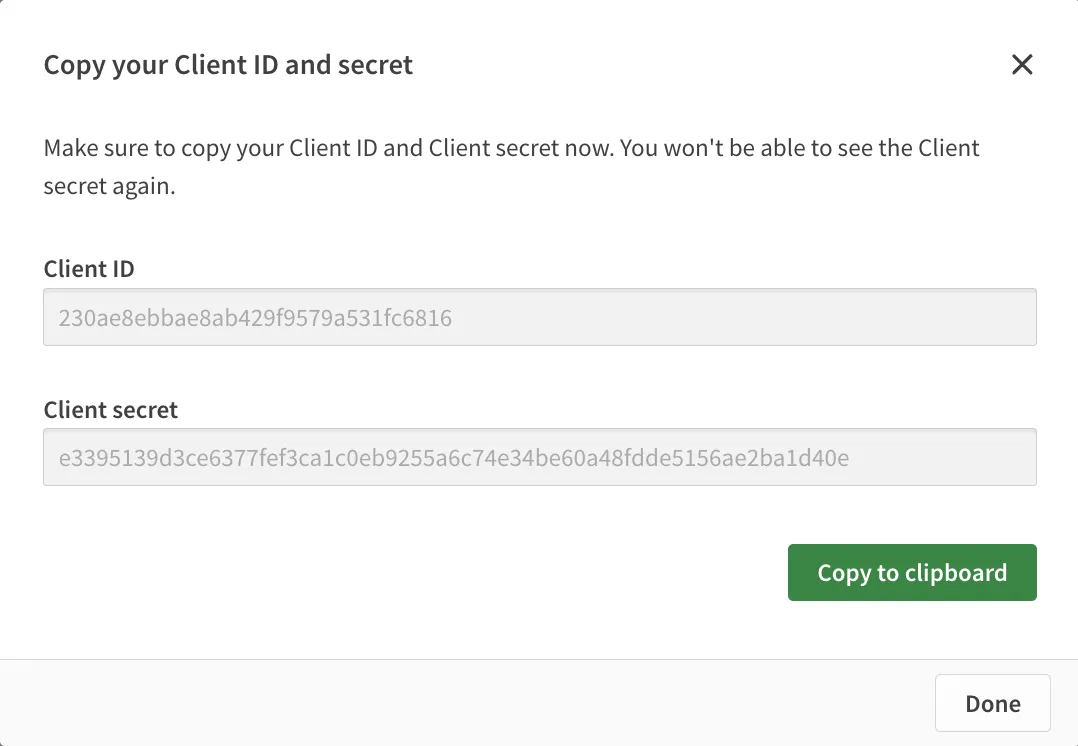
Click on the action menu (three dots) next to the OAuth2 client application entry and select Change consent method.
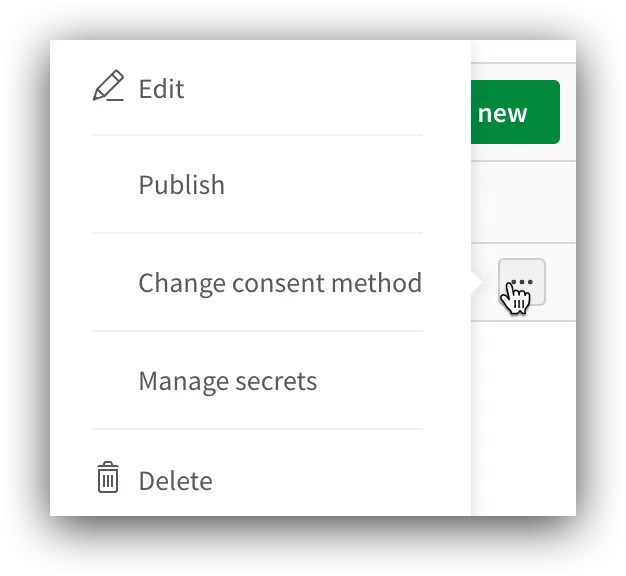
Select the Trusted option and click Change consent method.
The OAuth2 client configuration is complete. To use the configuration, add the Client ID and Client secret into your application where applicable.